In the age of the internet, technology is virtually inescapable in all walks of life. Even in very rural areas, some form of connection is necessary, whether for educational, professional, or personal purposes.
Now more than ever, companies (and even consumers) must realize and recognize how important it is to have security in all the programs they use.
This is even more important for business organizations, particularly those that specialize in creating and maintaining software. With the constant threat of leaked data, it is hard to be complacent, especially if the program is designed for sensitive data such as bank accounts and other personal information.
This is where Secure Software Development Life Cycles (SDLC) come into play.
What is the Secure Software Development Life Cycle (SDLC)?
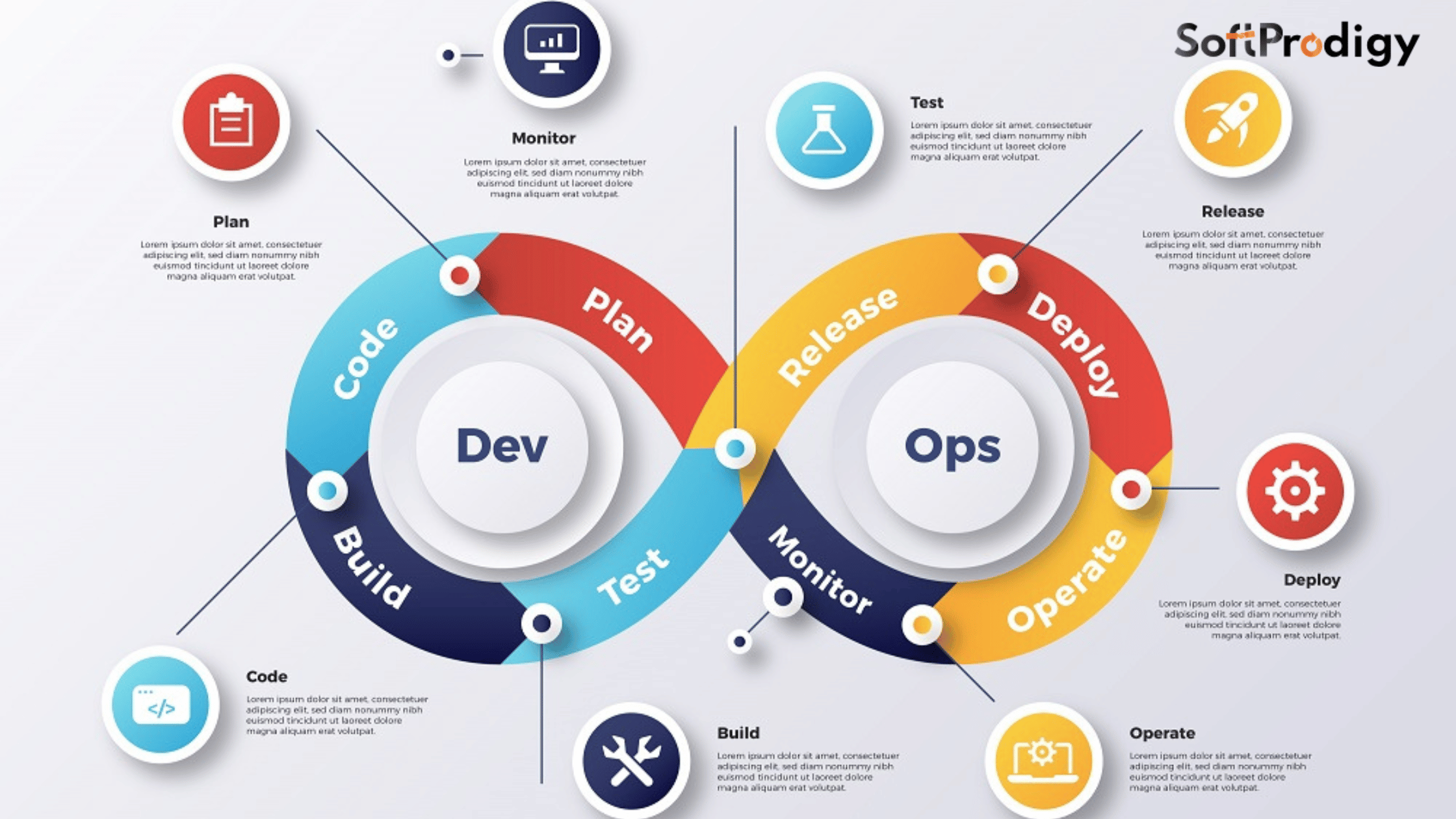
First things first, what even is a software development life cycle or SDLC? An SDLC is a framework used by organizations in order to facilitate the creation of an application or program. It lays out how the software will be completed, from the brainstorming of the idea right up to how it can be dismantled, from its birth to its demise. It is quite literally the life cycle of a program.
A few notable bare-bones soft development life cycle models are Agile, Iterative, Spiral, and Waterfall, among a lot of other options.
There are lots of ways to illustrate how an SDLC works, but generally speaking, most SDLCs look a lot like this:
- Planning
- Analysis
- Design
- Development
- Testing
- Release
- Maintenance
Key Differences Between Standard SDLC and Secure SDLC
We’ll talk a little about the framework later on. Before that, why is it important to not only have an SDLC, but also to have a secure one? The difference between a plain old SDLC and a secure SDLC is actually pretty simple to explain. It’s just that a secure SDLC has predictably more security-related steps in its process.
| Aspect | Standard SDLC | Secure SDLC |
|---|---|---|
| Primary Focus | Functionality, performance, delivery timeline | Functionality and integrated security |
| Security Integration | Security is often addressed late, during testing | Security is embedded in every phase of development |
| Development Activities | Requirement gathering, design, development, testing, deployment, maintenance | All standard activities plus threat modeling, secure coding, security testing, penetration testing |
| Risk Management | Vulnerabilities may be found late, increasing fix costs | Vulnerabilities are identified early and proactively addressed |
| Outcome | Functional software, potential hidden risks | Secure, reliable, and compliant software with reduced risk |
It’s not enough anymore to just perform the basic framework of SDLCs. Especially when handling sensitive information, it is vital to add security measures when developing these programs. By simply tacking on some security requirements to the existing model, you can take your software development life cycle to another level.
Several secure SDLC models are already used in the market. Some of the most well-known and well-used ones are Microsoft Security Development Lifecycle (MS SDL), NIST 800-64, and OWASP CLASP.
- MS SDL is a model developed by Microsoft and it highlights 12 ways for organizations to add security to their programs.
- The standards for NIST 800-64 was refined by the National Institute of Standards and Technology, and it features processes that can be assimilated into an organization’s existing SDLC framework.
- OWASP CLASP is by the Open Web Application Security Project (OWASP) Foundation, a non-profit foundation that strives for better software security. CLASP stands for Comprehensive, Lightweight Application Security Process. It was derived from the MS SDL, with the addition of mapping security activities to roles in a company.
SDLC Security Best Practices
SDLC security best practices strengthen software by weaving protection into every phase, reducing vulnerability discovery late in the cycle and lowering remediation costs. Below is a concise, practical expansion of each item with actionable steps.
Perform risk assessments early
- Identify crown-jewel assets, data sensitivity, trust boundaries, and potential threat actors during requirements and design to prioritize defenses where impact is highest.
- Use lightweight threat modeling (STRIDE or attack trees), define misuse/abuse cases, and assign risk scores (likelihood × impact) to guide security controls and test plans.
- Document security requirements alongside functional ones (e.g., encryption, authentication strength, logging, RTO/RPO), and make them acceptance criteria for delivery.
Adopt DevSecOps culture
- Shift security left and right: integrate security in planning, CI/CD, and runtime monitoring so it’s continuous rather than a late gate.
- Embed security champions in each squad, define clear ownership for vulnerabilities, and make security metrics part of engineering KPIs.
- Automate wherever possible (policy as code, dependency checks, secrets scanning) and create blameless post-incident reviews to improve learning cycles.
Implement code scanning tools (e.g., SonarQube)
- Use a layered approach: SAST for source code, SCA for third‑party/open-source dependencies, DAST for running services, and secrets scanning for credentials.
- Run scans in pull requests and CI pipelines with severity thresholds that block merges on critical/high issues; provide developer-friendly remediation guidance.
- Tune rules to reduce noise, baseline existing debt to avoid alert fatigue, and track time-to-fix and recurrence rates to improve signal quality over time.
Enforce security coding guidelines
- Standardize secure patterns for input validation, output encoding, authentication, authorization, cryptography, error handling, and logging.
- Maintain language- and framework-specific guides (e.g., Java Spring, Node.js, Python), and codify them as linting rules, templates, and secure libraries.
- Require secure code reviews with checklists mapped to common weaknesses (e.g., OWASP Top 10, CWE) and mandate tests for security-critical paths.
Provide regular team training
- Deliver role-based training: developers (secure coding, dependency hygiene), QA (abuse-case testing), ops (hardening, secrets management), product (risk trade-offs).
- Combine e-learning with hands-on labs and capture-the-flag exercises; refresh at least quarterly to cover new threats, frameworks, and org-specific incidents.
- Measure effectiveness via pre/post assessments, reduced vulnerability recurrence, and faster remediation times; align training to real findings from scans and pen tests.
Practical checklist to get started
- Define security acceptance criteria per user story.
- Add SAST, SCA, and secrets scanning to CI; block on critical issues.
- Stand up a simple threat modeling routine during design reviews.
- Create a lightweight, secure code review checklist per repo.
- Appoint security champions and track security SLAs in the backlog.
These practices help ensure vulnerabilities are found early, fixes are cheaper, and releases meet compliance and resilience goals without slowing delivery.
Benefits of a Secure SDLC
A secure SDLC embeds security into every development phase, yielding safer software, fewer production issues, and easier compliance across regulated industries. Each benefit below connects to concrete practices teams can adopt to realize the gains.
Stronger protection of applications
- Security is designed in from requirements to maintenance, so controls like authentication, authorization, encryption, logging, and input validation are consistent and defense-in-depth is achievable.
- Threat modeling and secure architecture reviews reduce systemic weaknesses (e.g., insecure data flows, missing isolation) that are hard to fix later.
- Secure coding standards plus automated checks (e.g., SAST/SCA) prevent common vulnerabilities such as injection, broken access control, and insecure dependencies from reaching production.
Early vulnerability detection
- Shifting left with code scanning in pull requests, dependency checks, and secrets scanning in CI catches flaws before merge and build stages.
- Security test cases and abuse cases added alongside functional tests surface logic and authorization gaps during normal QA cycles.
- Iterative threat modeling at design time highlights high-risk components early, guiding targeted testing and reducing last-minute surprises.
Cost efficiency
- Fixing issues during design or coding is far cheaper than remediation after release, avoiding hotfixes, rollbacks, and emergency patches.
- Continuous automation (pipelines, policy as code, reusable secure libraries) lowers manual effort and reduces regression risk across releases.
- Preventing incidents avoids direct costs (breach response, downtime, fines) and indirect costs (reputation damage, customer churn).
Compliance with standards (GDPR, HIPAA, PCI-DSS)
- Secure SDLC artifacts—requirements, risk assessments, test evidence, and change logs—create an auditable trail that maps to control frameworks.
- Built-in privacy and security controls (data minimization, encryption in transit/at rest, access controls, logging/monitoring) align with GDPR, HIPAA, and PCI-DSS expectations.
- Regular reviews, vulnerability management SLAs, and third-party risk checks help maintain continuous compliance across versions, easing audits and certifications.
Where Do You Go from Here?
If you or your organization are new to the whole “secure SDLC” scene, then no doubt that this is all a little bit overwhelming. To make things easier, here are a few things you can do to get started on improving your security, in no particular order:
- Get yourself and your colleagues updated on the secure SDLC framework best suited for your goals.
- Do an architecture risk analysis at the beginning of your project.
- Keep security in mind throughout the planning, up until the culmination of the program.
- For efficiency, utilize code scanning tools for dynamic analysis, interactive application security testing, and static analysis.
Way Ahead of You
Oh, so you already have a secure SDLC setup in your organization? More power to you, then! However, don’t forget that security is a constantly ongoing concern.
You can’t just sit back and relax after you successfully launch your software. You’ll need to stay on top of maintenance. More importantly, you have to make sure that the security measures you put in place do not become outdated.
You can also build on our existing strategy by taking a peek at how your neighbors are doing. Look into your method’s effectiveness by using programs that measure software security.
Programs such as the Building Security in Maturity Model (BSIMM). You won’t get a literal look into other organizations’ activities through this, but the BSIMM will show you which security programs are effective for your field.